Deploying Kong API Gateway
hashistack deploys Kong API Gateway in the following way:
- Deploys Kong API Gateway in HTTP mode
- Deploys a reverse proxy Nginx in front of the Kong API Gateway in the same EC2 to redirect all HTTPS request to gateway's corresponding HTTP ports
The diagrams below illustrates the resulting deployment
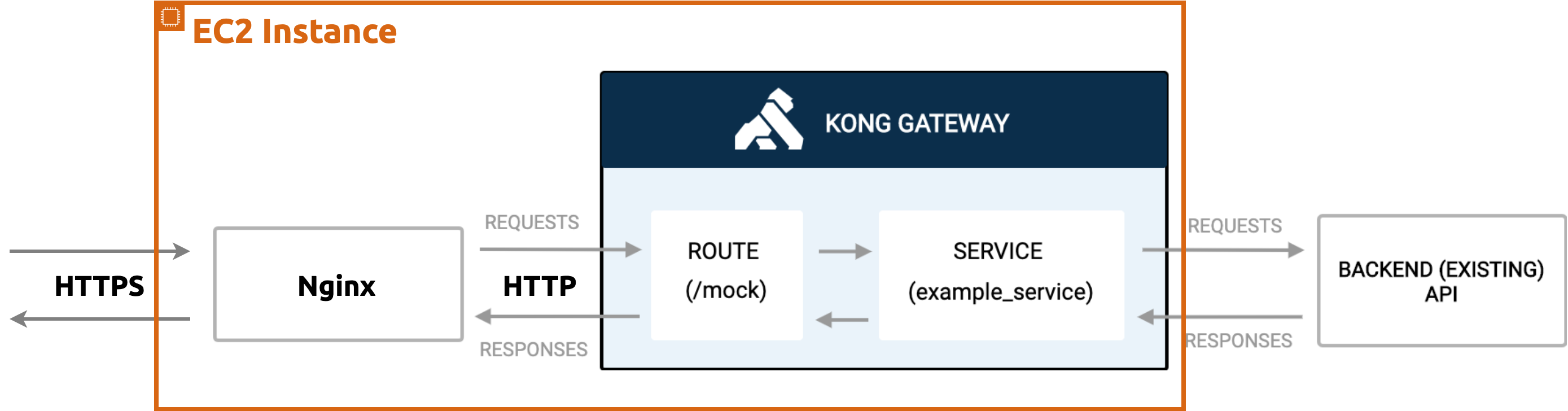
General Deployments
Please complete the general setup before proceeding.
hashistack uses a customized fork of docker-kong to fully separate the app and SSL, and, therefore, the Nginx config needs multiple servers to ensure all HTTPS ports are mapped to their corresponding HTTP ports as shown in the config snippet below:
All relevant HTTP and HTTPS ports are listed in Kong's documentation here. In general,
our Nginx should **listen on an HTTPS port and proxy_pass to an HTTP port. For example, ports 8443 and 8444 are
proxy_passed to 8000 and 8001, respectively, both of which are listed in the doc.
One special case is HTTP port 8000, which is the redirect port. hashistack maps the standard SSL 443 port to 8000 so that any downstream (such as UI web app) simply needs to hit the domain without specifying port number and have its request be reidrected to upstream services (such as database webservice)
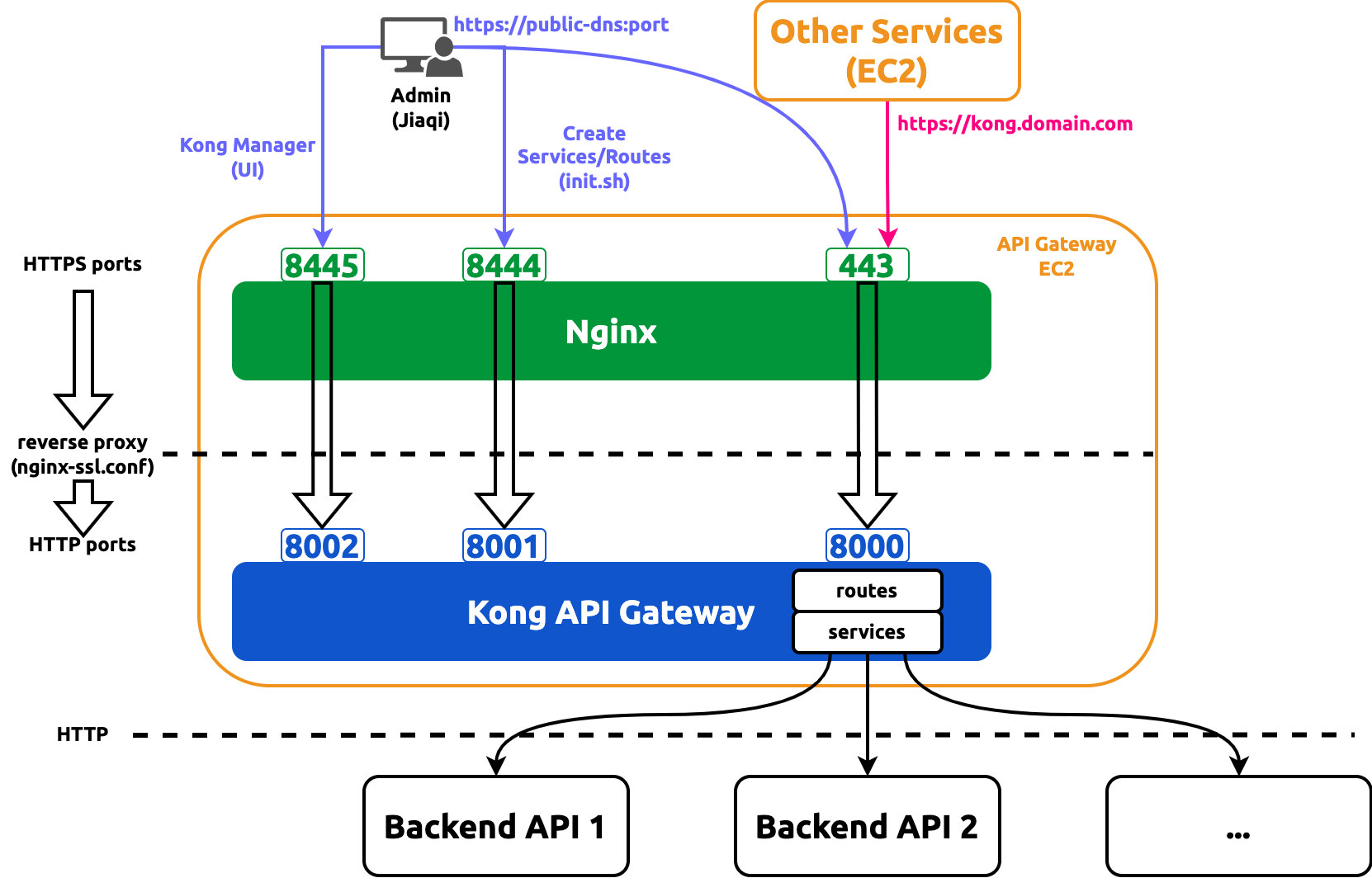
Defining Packer Variables
Create a HashiCorp Packer variable values file named aws-kong.auto.pkrvars.hcl under hashistack/hashicorp/kong-api-gateway/images directory with the following contents:
ami_region = "us-east-1"
ami_name = "my-kong-ami"
instance_type = "t2.small"
kong_api_gateway_domain = "gateway.mycompany.com"
ssl_cert_base64 = "YXNkZnNnaHRkeWhyZXJ3ZGZydGV3ZHNmZ3RoeTY0cmV3ZGZyZWd0cmV3d2ZyZw=="
ssl_cert_key_base64 = "MzI0NXRnZjk4dmJoIGNsO2VbNDM1MHRdzszNDM1b2l0cmo="
ami_regionis the image region where Kong API Gateway AMI will be published to. The published image will be privateami_nameis the name of the resulting AMI that will appear when managing AMIs in the AWS console or via APIs. This can be the same across builds, because hashistack will deregister the old AMI with the same name and replace it with the current built oneinstance_typeThe AWS EC2 instance type to use while building the AMIkong_api_gateway_domainis the SSL-enabled domain that will serve the various ports of Kong gatewayssl_cert_base64is a base64 encoded string of the content of SSL certificate file for the SSL-enabled domain, i.e. 'mygateway.mycompany.com' given thekong_api_gateway_domainis 'mygateway.mycompany.com'ssl_cert_key_base64is a base64 encoded string of the content of SSL certificate file for the SSL-enabled domain, i.e. 'mygateway.mycompany.com' given the kong-api-gateway-domain is 'mygateway.mycompany.com'
Defining Terraform Variables
Create a HashiCorp Terraform variable values file named aws-kong.auto.tfvars under hashistack/hashicorp/kong-api-gateway/instances directory with the following contents:
aws_ec2_region = "us-east-1"
ami_name = "my-kong-ami"
instance_type = "t2.small"
instance_name = "My Kong API Gateway"
security_groups = ["My Kong API Gateway Security Group"]
kong_api_gateway_domain = "gateway.mycompany.com"
route_53_zone_id = "MBS8YLKZML18VV2E8M8OK"
-
aws_ec2_regionis the EC2 runtime region where Kong will be deployed into -
ami_nameis the name of the published AMI; it must be the same as theami_namein Packer variable file -
instance_typeis the AWS EC2 instance type used for deployed infrastructure -
instance_nameis the deployed EC2 name as appeared in the instance list of AWS console; it can be arbitrary -
security_groupsis the list of AWS Security Group names to associate with (yes, not ID, but name...)infoThe following Kong ports need to be open by configuring the inbound rules of the included security groups:
- 80
- 443
- 8444
- 8445
-
kong_api_gateway_domainis the SSL-enabled domain that will serve Kong manager UIwarninghashistack will bind a private IP address to this domain for the following reasons:
- AWS security groups works for private IP only for DNS resolving. Services interacting with Kong gateway can use this domain.
- In the case of internal access, for example administrators visiting Kong Manager for config purposes, people can
still use
https://public-dns:port
-
route_53_zone_idis the AWS Route 53 hosted Zone ID that hosts the domaingateway.mycompany.comtipTo find the zone ID in AWS Route 53, we can:
- Sign in to the AWS Management Console
- Open the Route 53 console at https://console.aws.amazon.com/route53/
- Select Hosted zones in the navigation pane
- Find the requested ID in the top level Hosted Zones summary in the Route 53 section
Building AMI Image
cd hashistack
cp hashicorp/common/images/aws/aws-builder.pkr.hcl hashicorp/kong-api-gateway/images/aws
cp hashicorp/common/images/aws/aws-packer.pkr.hcl hashicorp/kong-api-gateway/images/aws
cd hashicorp/kong-api-gateway/images/aws
packer init .
packer validate .
packer build .
EBS volumes during build time will [automatically be removed][HashiCorp Packer delete_on_termination]
This will take a while and to save time, we can leave it here and proceed immediately to the next step.
Deploying to EC2
cd ../../instances/aws
cp ../../../common/instances/aws/aws-ec2.tf .
cp ../../../common/instances/aws/aws-ssl.tf .
cp ../../../common/instances/aws/aws-terraform.tf .
terraform init
terraform validate
terraform apply -auto-approve
Deployment via Screwdriver CD
hashistack supports deployment using Screwdriver CD. Please check it out.
Deployment via HACP
Please try our HACP platform to deploy a Kong instance. It gives us one-click experience that helps us stand up an API gateway in a minute.